Best Practices for Electronic Assessments
Background
We present an overview of best practices for conducting E-Assessments we have collected based on a survey by four lecturers from three different universities. We supplemented this data with insights from our own experiences, as we are a group of several lecturers with more than 15 years of experience in teaching. All the data was collected in 2017.
The following post is structured in a way, that the first chapter deals with the introduction and realization of E-Assessments in general and talks about the most important topics to cover if you want to introduce E-Assessments at your institution. The second part is dedicated to cheating prevention when conducting E-Assessments, since this is one of the main focal points in the context of E-Assessments.
Table of Contents
- Introduction
- Survey
- Realization of E-Assessments
- Cheating Prevention
- Conclusion
- Literature & References
- Resources
- Contact
Introduction

Almost all educators would like to believe that the material they have taught their students is actually learned by their students. But what is the best way to measure how much a student has learned? For hundreds of years, “testing” knowledge and skills was primarily surmised by giving the students an assessment or test, which was either a midterm examination or final examination. Although these assessments can take many forms, including oral exams or lab practical, often it is in the form of a paper assessment, where tasks can be multiple choice, fill-in-the-blank, drawings, text answers, etc. With the advent of Information Technology (IT) and the Internet, assessments can also be given electronically. Electronic assessment, also known as E-Assessment, refers to evaluation methods and practices that emphasize the role of IT relative to measuring students’ learning.
Origins
The use of computer technology in educational assessment has a decades-long history. Computers were initially adopted for assessment in the 1970s in order to reduce human’s workload to mark examinations and rate scoring. Since then, assessment has progressed in conjunction with IT advancements and the arrival of the Internet in education. Nowadays, it is widely recognized that E-Assessments can bring benefits at both administrative and pedagogical levels. As more and more learning activities run on Learning Management System (LMS) such as Moodle, both teachers and students get familiar to using such systems.
Building Blocks
For the purpose of this blog post, we consider an “E-Assessment” to be a summative examination in higher education in an engineering discipline. Implementing such exams includes four main building blocks, which we will discuss throughout this blog post: general setup, exam content preparation, exam conduction, and exam grading.
Advantages
E-Assessments have several obvious and well-known advantages, such as providing objective automatic grading, instant scoring and feedback, storage and reusability, and scalability. In addition, assessments on computers offer the advantage to ease the reading of long text answers compared to handwriting papers, and IT solutions also allows for a wider range of tasks and activities that can enable teachers to evaluate their students in the appropriate environment for summative assessments. Finally, mobile and tablet devices provide new opportunities for formative E-Assessments, like using clickers (audience/personal response systems) in large classroom environments.
Challenges
On the other hand, educators have several aspects to consider when moving to E-Assessments, including: differences in preparation and conduction of the exam; prevention of cheating; changes in scoring schemes; and modified feedback mechanisms. Developing an online examination requires defining tasks that will allow to verify the student’s’ skills in the appropriate context, and providing a technological setup and framework that is able to support the E-Assessments (tools, network, and computers). It also requires the examiner to acquire the competencies to properly use digital tools and media and the LMS. In order to avoid technical issues during the conduction of an E-Assessments, an IT hardware is required that can handle large numbers of student at the same time. One of the most important aspects is to prevent access of students to unallowed external help (humans) or resources (teaching material, internet) during the exam (cheating prevention). There exist several technical frameworks, such as Safe Exam Browser, that try to restrict and secure the computer’s usage and reduce students’ abilities to behave dishonestly during an E-Assessment.
Survey

We launched an international survey among university lecturers in order to gather insights and best practices for E- As. Despite wide distribution of the survey at several universities in different countries (more than 500 addresses), only 18 lecturers answered, most of them from Switzerland (11), followed by Germany (2), Australia (2), France (1), Greece (1) and South Africa (1). Participants were primarily masculine (88.2%), and most of them were between 35-45 years old (77%), with an equal distribution of ages below 35, between 46-55 and 56-65 years old (6.7% each).
The most important results are as follows:
- E-Assessments concerns a wide range of fields: Applied Statistics, Language Translation, Electrical Engineering, English for Law, Programming and Digital Technologies, without any domain emerging significantly from the others.
- E-Assessment is mainly implemented at the bachelor level. Regarding class size, it is almost equally used (around 20%) in classes with 15-30 or 30-60 or 60-100 or 200-400 students.
- Multiple choice and short text answers are preferred to long text, calculation and yes/no answers.
- No auxiliary material is allowed in 50% of the E-Assessments. When it is authorized, students can refer to other printed material, lecture notes, electronic notes, or they can open an Internet access to specific domains.
- Most participants used Moodle as LMS platform for E-Assessments.
- Introducing E-Assessments did not change the duration of the examination, which can be long (120 minutes), but it increased the preparation time and decreased the grading effort. The participants indicated that the main benefits of E-Assessment are (in decreasing priority) automatic grading of exams, statistics related to the exams outcomes, storing and reuse of exercises, and storing results (digital archive).
- In order to prevent technical difficulties, 69% of the participants provided spare machines and sometimes dedicated technical staff. In addition, 15% of them ran mock E-Assessments.
One important and often-mentioned aspect was cheating prevention: Almost all participants implemented actions to prevent dishonest behavior of the students. Methods are relative to IT technology (such as no internet access, use of Safe-Exam-Browser, randomized questions, screen control), or relative to the environment (such as dedicated PC organization in the classroom that stops students’ exchanges), or relative to the general circumstances (such as a strict time limitation and providing enough problems so that solving more tasks is more attractive than cheating). Participants generally agree that compared to pen-and-paper exams, E-Assessments require more effort to avoid cheating, so it appears to be a major issue. Unlike E-Assessment preparation, which efforts reduce with repeating exams practise, the efforts to prevent students’ dishonest behavior appears to remain.
Realization of E-Assessments

In this section, we give an overview of scientific state-of- the-art, tools, resources and best practices for each of the building blocks for implementing an E-Assessment – except for cheating prevention, which is described later on in a separate chapter due to its significance.
General Setup
The step of defining the general setup has the largest impact in the process, especially if E-Assessments are conducted in a summative form as in the context of this study. Many conditions must be considered, among others the infrastructure, e.g. if there are enough institution computers or Bring Your Own Device (BYOD) must be required. Some universities provide special E-Assessment rooms with over 100 work places (e.g. www.eassessment.uni-bremen.de) which offers a very stable setup, while others utilize “mobile” setups with computers or tablets. Still, these choices can be constrained by money, space or human resources available, but also by factors identified within a risk analysis, such as “Denial-of-Service” attacks on the network, storage weaknesses, power shortage, computer problems, etc. On the othe, the selected software framework should usually comply with following criteria: visual impression, ease of use, ease of setup, short- and long-term costs, robustness, high-security standards. Often employed systems are LMS since they naturally continue electronic courses; most common are Moodle, ILIAS, and OLAT. However, direct E- As system exists, e.g. DEWIS (dewis.uwe.ac.uk), Q-Exam (www.q-exam.net).
Also important are legal aspects, which can complicate and pose further conditions on the general setup. These conditions generally refer to aspects like security and duration of exam storages, legal appeal to e-exams because the used framework/setup, but also security (assurance of student identity) issues must be cleared.
These restraints can limit methods, although, for example in the exam content preparation, there is an explosion of methods that can be used, as audio, video, virtual reality, simulation, drawing, programming tasks, additional material as open book or even the internet, enabling students much more possibilities than with paper and pen. When the physical and software setup is defined and the legal context is cleared, a carefully exam preparation is due.
Exam Content
Each exam should be designed with a theoretical background on didactics, considering different aspects such as: competency assessment, learning goals, exam objectivity, and taxonomy of educational objectives. Further, providing access to a computer enables, as indicated above, a variety of other media, increasing the input and possibilities of an exam, thus allowing students multiple (sensorial) access to the content.
Thus, this additional material or media can have a pedagogical impact as well or even be necessary; just as interpreters, who render one language into another orally in real time, need audio samples to perform. Software studios enable the students to solve more difficult problems in a period of time, which might fit within an E-Assessment, especially with regards to simulation, programming and mathematics. However, typical question types for E-Assessments are still technically very simple: free text (short or long), hotspot, drag and drop (graphical or text), analogy questions, selection list, causality questions, multiple choice (table, multiple, single), answer pairs.
Exam Conduction
The examiners and exam conductors must be instructed into the framework and trained or briefed for technical problems, especially if additional media/software is involved. An obvious solution would be to offer the exam as paper, but that is problematic when using media; still some students might prefer a paper solution. Further, additional computers, as backup, can usually be only made available in a certain contingent.
Nonetheless, another point of view on the examination should be taken into consideration: “many students cited the usefulness of mock e-exams”. Such mock e-exams help the students to familiarize with the system and adjust the expectations on the tests (from both sides, students as lecturers).
Exam Grading
The last step is grading. There, is an expectation on saving time and costs but also having more freedom and at the same time objectivity. The freedom regarding location (home-office) and different possibilities to marking, especially, to achieve objectivity more easily through semi/automatic grading. Furthermore, data mining methods can give more insights about the course, such as on student performance (as for example the language in free-text answers can be analyzed), but also highlights more easily the difficulties in the exam (e.g. readability of the questions).
Since multiple questions are easy to automate, they are very often employed and provided by many frameworks in multiple variations. However, it is a controversial question type. Usually, the more degree of freedom of the answer the more difficult it is to mark it, especially when automating. Already for semi-structured questions, as filling the blanks or numeric values in mathematical questions, the answers must be normalized. This is a laborious task (finding synonyms, formatting numbers: 0.35=3.5E-1, etc.), and can be very difficult to solve. Interestingly, there are some approaches for semi-automatic grading, where similar answers are grouped together, pursuing same marking quality, and even approaches of automatic grading on free-text answering using deep learning. Although, machine learning and artificial intelligence can provide more objectivity in grading, there are a myriad of examples where these technologies, when applied autonomously, failed and therefore are not widespread.
For programming courses, there are in principle two ways to tests the results for correctness: black-box or white-box testing. Whereas, black-box testing with input-output – e.g. as performed by a variety of Moodle’s plugins (e.g. vpl.dis.ulpgc.es) – poses a very specific expectation on the result of the student’s program, missing a measurable value for how much a solution is wrong, depriving a student of a valuable input. In turn, white-box testing is a difficult task, and in combination of code style can be compared to written essay examination, where not only result but the way it is written becomes a central point in the evaluation.
Cheating Prevention

In our opinion, one of the biggest problems when conducting E-Assessments is the larger potential for students to cheat using the electronic devices. In the following section, we are going to discuss different aspects of this problem and then follow up with advice how potential cheating can be mitigated.
Classical Cheating
In any exam, be it electronically conducted or not, the students might try to cheat in “classical” ways. We call them “classical”, because such ways of cheating can also be exploited when doing a pen & paper exam. These include:
- Talking to the neighbour
- Passing notes around
- Cheat sheets
There are numerous other ways, but we won’t list them all here since the reader is certainly familiar with the problematic. These ways of cheating must be tackled the same way as in a classical exam: By using an attentive supervisor, putting sufficent table space between the students, etc.
Cheating with Internet Access
If students have access to the internet, the have access to unlimited sources of information, such as encyclopedic websites such as Wikipedia or WolframAlpha, textbooks (e.g. Google Books) or research articles (e.g. Springer Link or ResearchGate), but also Question-Answering websites such as Yahoo Clever, Quora or StackOverflow .
However, Internet access also introduces the problem of communication with others while taking the exam, which is even more severe, because communicating with others is usually strictly prohibited. Internet connectivity enables exactly that: students can communicate with each other through messaging channels (e.g. E-Mail, WhatsApp); they might seek help via Q&A websites such as Quora or StackOverflow; or they can even communicate with dedicated external experts, which allows them to “outsource” the solving of their exam. In an extreme case, one could imagine that a student simply sends, say, the PDF of the exam tasks to an expert, which then in turn solves it and sends the solutions back to the student.
Finally, network connectivity also allows for direct access to the students’ computer, for instance via shared screens or remote desktop access, e.g. with TeamViewer (www.teamviewer.com). Here, a third person can read and fill out the entire exam directly via the student’s computer.
Depending on the technical infrastructure of the institution, such problems can be mitigated quite easily. For example, if the network infrastructure of the institution allows to block certain ways to communicate (e.g. disable TeamViewer, only allow access to certain websites). But there is a big however in case of BYOD setups: With the ubiquity of smartphones and with mobile networks getting better and better by the day, another problem is that the student might not even use the internet access provided by the institution. They could simply use their smartphone and start a so called Ad-Hoc Hotspot, which allows them to access the internet without ever going through the network infrastructure of the institution, but instead use the internet access of their smartphone. This problem cannot be mitigated easily, because there is no simple way to block smartphones from being able to access the internet, besides hosting the exam in a completely isolated room, where no signals can enter or leave. But this is not practical in most situations.
We even considered using a so called jammer, which interferes with the signals sent from and to electronic devices and blocks them effectively. However, in our research, we quickly found out that such devices are strictly prohibited in most countries (e.g. Europen Union, United States of America).
Technical Devices
There are two different ways how E-Assessments can be conducted with respect to the devices used (typically computers or tablets): first, the traditional approach is to use devices provided by the institution where the exam is conducted (institutional devices). In such a setup, cheating is a problem and must be tackled by implementing technical and organizational measures, but most of the potential attacks can be limited or mitigated because the devices are managed by the institution itself. This allows to ensure that, for example, no prohibited software is installed, there is no or only restricted internet access, and monitoring software can track potential modifications of the basic system setting.
Cheating also has to be prevented when using institutional devices. But the main difference in using such devices instead of the students’ devices is that they are managed by the institution. Hence, most of the potential attacks against the system cannot be easily performed because the students do not have access to the devices before the exams start. For this reason, we are mainly going to discuss measures which can be used to prevent cheating in “Bring Your Own Device (BYOD)” approaches.
The second type is BYOD scenarios: In this case the students work on their own devices. This is usually the same device as they have used throughout the semester. This implies that the students have all of the resources they gathered in a certain course (e.g. scripts, exercises) available on their device, if desired. This is usually not a problem in an open-book assessment, but it already poses an issue if the exam is supposed to be closed-book. But, even more fundamental problems arise when internet access has to be restricted or forbidden, since the examiner does not have full control over the installed software on the devices.
In the following paragraphs we will discuss two technical measures that may help to mitigate these issues. These measures are applicable with both BYOD and exams taken on institutional devices. However, we will focus more on the BYOD case, since enforcing policies on personal devices is usually more difficult than on institutional devices because of the lack of control and oversight.
Countermeasures
In the following section, we are going to provide countermeasures for the problems with cheating we have described before.
Lock-Down Software
The first solution we consider is a so-called “lock-down” or “kiosk” software. This is a special application, which, when started, locks down the device. This means that only the lock-down software is run and the user, or in this case the student, has no access to any other resource on the device (unless explicitly allowed). This allows to do a closed-book exam in a BYOD setup, where the institution does not have full control of the devices.
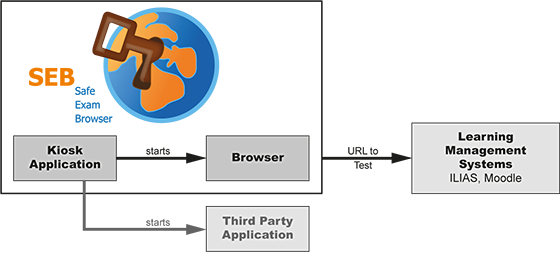
Lock-Down Browsers: The most common lock-down software comes in the form of lock-down web-browser. In most situations, such a lockdown browser is then used in combination with an LMS, such as Moodle or OLAT, where the students take their E-Assessments. One example of such software is the “Safe Exam Browser” (SEB) developed at the ETH Zurich, which was specifically developed for E-Assessments. Most of the time, the SEB or similar software is used in E-Assessments conducted on institutional devices, and it has already successfully been used in such settings at different universities. However, we evaluate SEB in the context of BYOD setups, where such a lock-down software would be installed on the devices of the students to control their access to additional resources (e.g. files, internet). There is more similar software on the market, such as the following:
- QuestBase Secure Browser
- SoftwareSecure Secure Exam Browser
- Respondus LockDown Browser
- SoftwareSecure SecureExam Browser
They provide features similar to the SEB, but are proprietary rather than open source as SEB. In the following two sections, we are going to talk about the features and also the security problems such lock-down browsers have. We are going to focus mainly on SEB for these discussions, but most of it should also apply to other lock-down browsers.
Architecture of the SafeExamBrowser software (https://blogs.ethz.ch/jlaville/ucl-diary)
Restricting Access to Resources: The SEB allows the lecturer to create a specific configuration for an E-Assessment, where the lecturer can specify various different parameters, such as the following:
- Software which the student is allowed/disallowed to use.
- Black-/Whitelists for URLs to visit with the browser
- Specific password for quitting the lockdown application.
Using these configurations, the lecturer can control which resources are available and accessible on the computer during the exam – as long as the SEB is running and active. Ensuring that the SEB runs, it is of paramount importance that it cannot be simply closed by the user (i.e. the student). For this reason, important part of a lock-down browser is the disabling of possibly “harmful” system commands to exit it. For example, on devices with the Windows operating system, keyboard commands, such as CTRL+ALT+Del (locking the device) or ALT+Tab (switching applications) must be disabled. This ensures that the student cannot exit the lock-down mode without either knowing the exit password or restarting its device. But here also lies one of the main problems, which most lock-down browsers have in common: If one restarts the device, the lockdown browser will not automatically restart itself after start-up. Hence, students who are struggling in an E-Assessment may be tempted to restart their device for getting access to the other resources available on their device. Even though this is easily noticeable by an attentive supervisor, it is still a problem when an E-Assessment with several hundred students is taken, since having oversight for all of them either requires an extensive number of supervisors.
Lock-down browsers also may have other problems. For instance, for the SEB we identified the following two potential vulnerabilities: One can control a system where SEB is running on a Windows machine from remote via the “Remote Desktop Protocol”. This allows third persons to view and even act on the student’s screen. SEB’s source code is publicly available via GitHub. This leads to a problem because tech-savvy student can download the code, modify it (e.g. disable security-features) and build its own version. This problem also applies to closed-source software to some degree, but modifications are much more easily applied in open-source software.
| Summary for Lock-Down Software | |
| Pro | Contra |
|
|
USB-Bootable Linux Distribution
Another idea to safely ensure that the students are only able to access resources they are allowed to do in a BYOD setup is by using a specially crafted image of the Linux OS, which can be loaded from a USB thumb-drive without the need to install it on the device itself. The idea behind it is, that a tech-savvy lecturer or an IT employee prepares a. image of the Linux OS, where all the prohibited features (e.g. internet access, calculator, etc.) are disabled. This version is then put on a read-only USB thumb-drive, from which the operating system can then be booted without the need to install it on the hard-drive of the devices it is run on.
This approach has some obvious advantages over the other approaches:
- No installation process is required, simply insert the USB thumb-drive and boot from it, that’s it.
- Everyone work with exactly the same software environment.
- The features accessible can be exactly defined by the person creating the OS image.
However, as good as it sounds, this approach also has a lot of drawbacks:
- Even though everyone works in the same software environment, there certainly are students which are much more adapted to using Linux in comparison to their colleagues, who, for example, use Windows on a daily basis.
- Having one operating system run on a wide range of devices, such as in BYOD approaches, requires extensive testing and even then there might be some problems related to the specific hardware the OS runs on. Also, some students might not even be allowed to boot another operating system for security reasons if they are using a business notebook provided by the company they work at.
- Preparing and maintaining such OS images is time consuming.
- In some cases, the students might be more familiar with the OS than the person preparing the image. This can lead to the problem, that the student might be capable of circumventing security measures put in place to prevent cheating.
- Preparing and distributing the USB thumb-drives for a large number of students poses organizational problems.
To the best of our knowledge, there are no prepared images of OS available, which are solely targeted at usage in the context of E-Assessments. However, there is for example the Lernstick developed at one of the educational colleges here in Switzerland. It primarily aims to be used as a quick to start environment for various different activities in classrooms, such as preparing presentation, drawing or writing texts, but it can also be used in the context of an exam.
| Summary for USB-Bootable Linux Distribution | |
| Pro | Contra |
|
|
Screen Recordings
Another way to prevent cheating in a BYOD setup is to simply record the screens of students’ devices and store these recordings. They can then be used to check whether the student has cheated, in case any suspicion arises. There are two main ways on how to record the screen of students: Either via software or via physical cameras.
Software Recordings: When using a software solution, in order to record the screens of the students, they have to install a recording software on their devices. Popular examples of such software are the Open Broadcaster Software (OBS, https://obsproject.com), or ObserveIT (www.observeit.com). When the exam starts, the students start to stream the content of their screens to a specified backend server in the network. This brings the benefit that the students can be monitored while the exam is conducted, and the screen contents can be evaluated on the fly, which potentially allows to detect dishonest behavior early. The backend server then stores these streams in the form of videos, which the lecturer can look at later.
Software recording sounds simple and promising at first sight; however, there are several potential issues which arise: First and foremost, the approach only works if the network is stable, otherwise the stream does not make it to the backend server and, hence, no video is recorded. The bandwidth required for a large number of students streaming simultaneously must not be underestimated: A preliminary test using the mentioned OBS client with an nginx Server (https://nginx.org) as the backend showed that streaming a video with a resolution of 720p and 5 frames per second on 200 devices requires around 400-500 gigabytes of storage (and corresponding network bandwidth).
Further, a major issue is that an actual backend service has to be implemented and maintained, which leads to additional costs. In additions, tech-savvy students might be able to circumvent such a software recording technology, for example by streaming a pre-recorded video instead of their actual screen content, running it inside a virtual machine. In principle, there are countermeasures for each of these attacks, but similar to the lock-down software, there is no total security.
Finally, one major issue is related to privacy. Depending on the country, it is prohibited to record the activities of students on their computer during the exam. This depends on the privacy laws of the country and has to be clarified before setting up the exam.
| Summary for Software Recording | |
| Pro | Contra |
|
|
Physical Cameras: The basic setup is straightforward: simply distribute the required number of cameras throughout the room where the E-Assessment is taken, so that all students and their devices are filmed from behind. The main benefits of this solution over the direct recording of screen via software is that it is much less vulnerable to technical problems or attacks, such as network connection drops or problems with installing the software on the students’ devices.
The main problem of physical cameras is that it cannot be guaranteed that the screens are always recorded, because the students may sit in different positions while taking the exam, which can lead to their bodies blocking the line of sight between the camera and the screen. In addition, similar to screen recordings there are privacy issues to consider, which are even more severe in this setting, since the cameras do not only record the exams itself, but also the students in person.
| Summary for Physical Cameras | |
| Pro | Contra |
|
|
Conclusion
The science of E-Assessments is a rapidly changing field, with new methods and technologies in development. Although there was not a large sample size, the survey results coincide with what exists in the literature, particularly that students prefer multiple choice and short text, that professors prefer E-Assessment as it decreases time spent grading, and that professors take measures to decrease any academic dishonesty that could potentially take place during the E-Assessment.
One major issue in E-Assessments is cheating prevention, since access to the Internet allows for new ways of dishonest behavior in comparison to pen-and-paper exams. Preventing cheating requires extensive technical and organizational measures in any case. We have shown several technical measures such as screen recording or lock-down browsers to prevent cheating when the exam is conducted on the students’ computers. Each of these approaches has its own set of vulnerabilities and drawbacks, which allow students to possibly circumvent the preventive measures.
The best solution at present is, in our opinion, a combination of several technologies, such as combining a lock-down browser with recordings by physical cameras. The lock-down browser drastically raises the amount of effort a student must exert in order to cheat, while the cameras are a strong threat that cheating might even be detected after the exam.
Literature & References
You can find all references and literature we have used to write this blog post in our paper, which you can find here.
Resources
The blog post is based on the following publication:
- Publication: Best Practices in E-Assessments with a Special Focus on Cheating Prevention – von Grünigen, Benites, Pradarelli, Magid, Cieliebak – EDUCON18. Dirk von Grünigen, Fernando Benites, Beatrice Pradarelli, Amani Magid, Mark Cieliebak. EDUCON 2018.
- Raw Survey Data: Best_Practices_E_Assessments-External_Survey_Results.xlsx
A link to the officially published paper will be placed here as soon as it becomes available.
Contact
In case you got any questions regarding this blog post, the paper or E-Assessments in general, you can simply get in touch with the authors of the paper by e-mail:
- Dirk von Grünigen, vogr@zhaw.ch
- Fernando Benites de Azevedo e Souza, benf@zhaw.ch
- Beatrice Pradarelli, beatrice.pradarelli@umontpellier.fr
- Amani Magid, amani.magid@nyu.edu
- Mark Cieliebak, ciel@zhaw.ch